Client Credentials
Introduction
Client Credentials are what your Application uses to prove its identity to the Eagle Eye Networks Cloud and authenticate when calling the Video API Platform. Every set of credentials is always tied to a specific Application, which makes Applications the natural boundary for managing access, permissions, and lifecycle controls like rotation or revocation.
This section covers how Client Credentials work, when to create multiple credential sets for the same Application (for example, separating environments or services), and how permissions and authentication flows—such as machine-to-machine access—are applied. You’ll also find practical guidance on storing credentials securely, rotating them without downtime, and troubleshooting the most common authentication issues.
End Users Should Never See Your Client CredentialsClient Credentials are how the Eagle Eye Video API Platform identifies the specific application that is accessing an end user account. End users should never have to create or enter Client Credentials as part of any integration process. The application developer should be the only entity with access to such credentials.
Creating Client Credentials
Client Credentials can be created and managed from the developer portal’s My Application page. After logging in to your developer dashboard, navigate to the List applications page to see all your existing applications.
From the Application List, find the application you want to create Client Credentials for, and click the See Client Credentials button next to the application name.
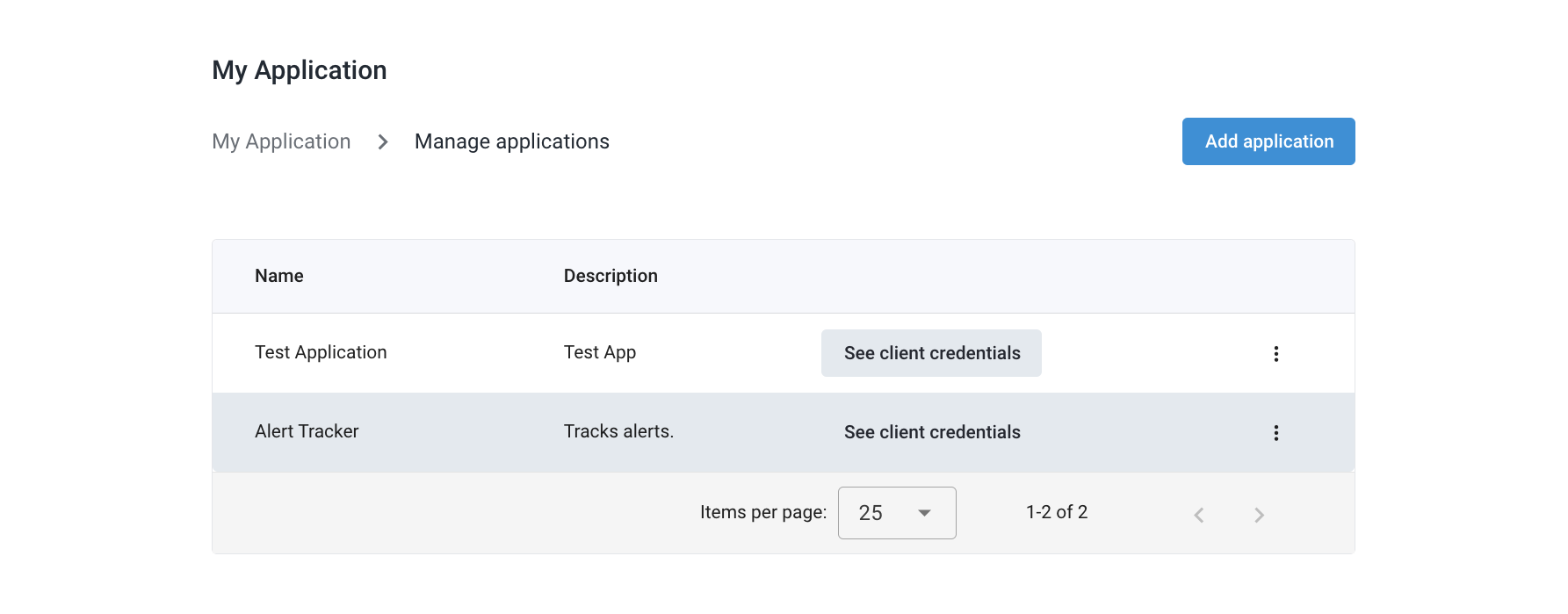
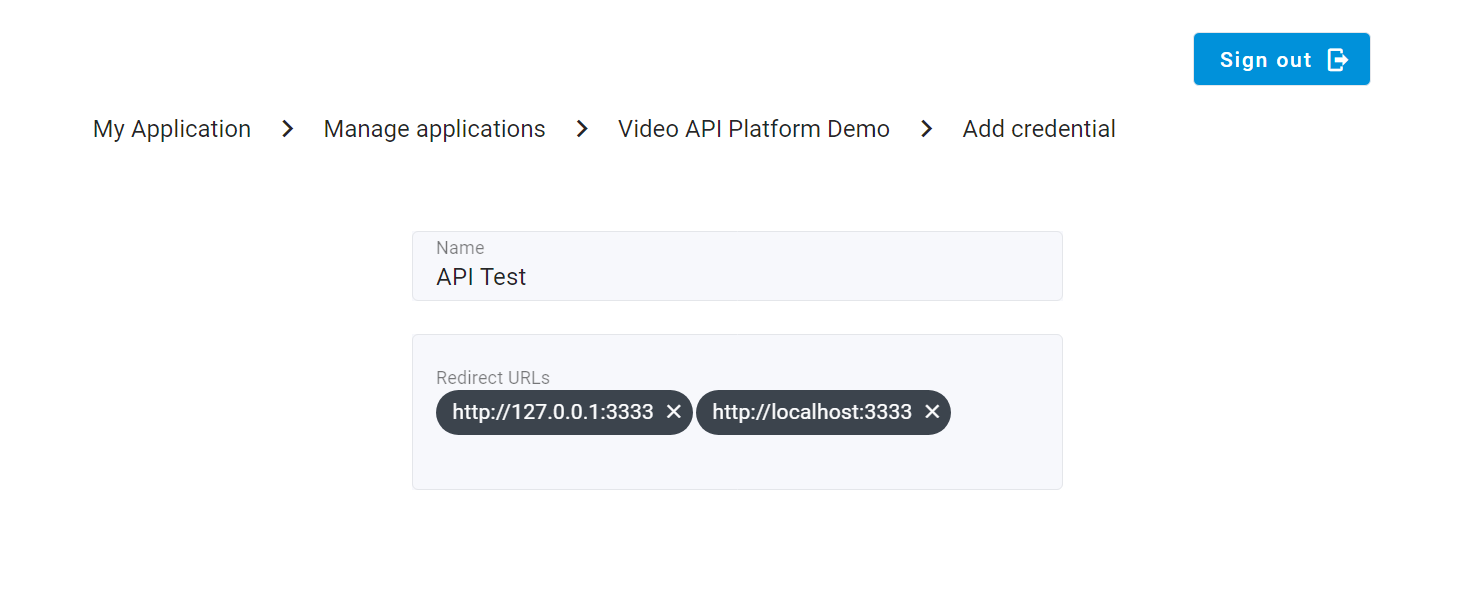
Once you reach the Client Credentials page, click the Add Credentials button on the top right to open the Client Credential Creation form. Fill out the required fields, including the credential name and redirect URLs.
Redirect URLsRedirect URLs are the locations where the Eagle Eye Networks authorization server will send the user after they have approved your application to access their resources. You must specify at least one redirect URL when creating Client Credentials.
sequenceDiagram
autonumber
participant U as User
participant B as Browser
participant A as App
participant AS as Auth
participant API as API
A->>B: Redirect to /authorize
B->>AS: GET /authorize
U->>AS: Login and consent
rect rgb(255, 245, 200)
AS-->>B: Redirect to callback
end
A->>AS: POST /token
AS-->>A: access_token (+ refresh_token)
A->>API: Bearer access_token
API-->>A: Protected resource
Managing Client Credentials
After creating Client Credentials, you can view and manage them from the Client Credentials page. Here, you can see all your Client Credentials, edit their details, and rotate or revoke them as needed.
To edit the details of a Client Credential, click the three-dot menu next to the credential name and select the Settings option. From here, you can update the credential name and redirect URLs.
Updated 2 days ago